A ransomware gang’s internal drama leaked after it backed Russia
The data leak laid bare unprecedented details of attack infrastructure, Bitcoin addresses, as well as internal conflicts and accusations.
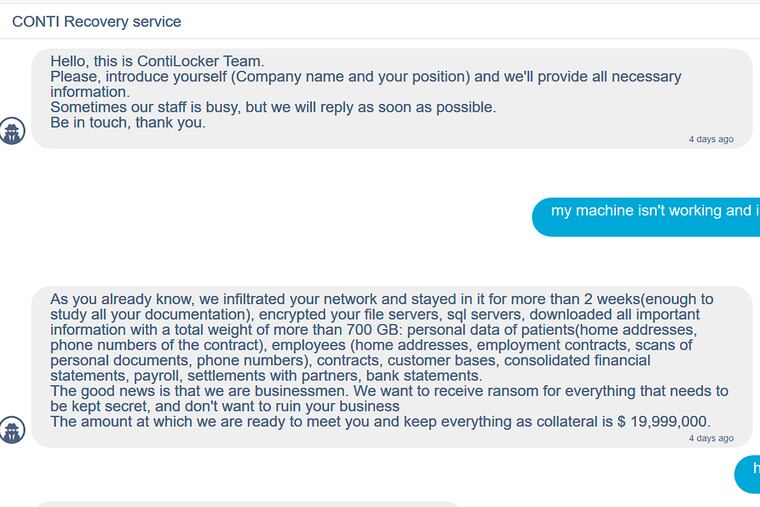
One of the world’s most successful ransomware groups is reeling from a massive dump of its own internal data after the cybercriminal gang aligned itself with the Russian government.
Conti, a cybercriminal group that researchers say is based in Russia, has extorted millions of dollars from U.S. and European companies in recent years. It provides affiliates around the world with malware that they deploy against victims in exchange for a cut of the ransom payments.
The data leak, which lays bare unprecedented details of attack infrastructure, bitcoin addresses, as well as internal conflicts and accusations, might never have occurred if the ransomware group Conti had chosen to stay apolitical, said Alex Holden, the chief information security officer for cybersecurity firm Hold Security.
“The main thing is that the gang itself contained a number of Ukrainians; it did not differentiate between its members,” Holden said. That changed last week after Russian forces attacked Ukraine, shelling military airbases, attacking checkpoints, and killing at least 137 Ukrainian troops.
While the Russian ground invasion played out on television screens around the world, a cyber conflict has occurred in parallel. Hackers on both sides of the conflict launched brute force attacks known as distributed denial-of-service attacks to knock government websites offline.
By the end of last week, Conti surprised many by firmly planting itself in Russian President Vladimir Putin's camp, saying it would use "all possible resources to strike back at the critical infrastructures of an enemy." The announcement caused a fissure within the group, cybersecurity analysts told Bloomberg News, which counts members from Russia and Eastern Europe among its members and affiliates.
"Most Russian-language underground forums don't allow discussions related to political topics," said Oleg Bondarenko, a senior director on the research team at Mandiant. "All such threads are quickly deleted by administrators," and some forums ban accounts that talk of targeting Russian-speaking countries, he said.
Conti issued a more muted announcement soon after its initial message, saying that although the group didn’t ally itself with any particular government, it would direct resources at “Western warmongers” and avenge any attempts to target critical infrastructure in Russia or any Russian-speaking region in the world.
"Ransomware is a global operation," said Allan Liska, an intelligence analyst at Massachusetts-based cybersecurity firm Recorded Future. "You may be based in Russia but you have to take into account all of the affiliates that are spread out all over the world right now, most likely, who are not fans of Russia. So you can't take a stance like that and not expect there to be blowback."
The blowback, he said, came in the form of chat logs and internal recriminations that dated back 13 months bleeding out into the public with the data leak.
“I’ve found 150-plus bitcoin wallets. There’s a whole lot of analysis to be done with that,” he said. The back-end infrastructure that Conti administrators or affiliates used during ransomware attacks were now out there “for governments or cybersecurity companies to start poking to find weaknesses.” While internal structures could be changed, “now we know what the back-end structure looks like, and we know what to scan for, what to look for when they move it,” he said.
Investigators have previously used financial data, such as cryptocurrency wallet addresses, to map ransomware hackers’ activities, and in some cases seizing extortion funds. Technical data give security personnel clues on how to block potential Conti hacks in the future.
Hold Security’s Holden also described what he’d been able to see of the leak. “We see the financial operations, we see their aspirations, for example, they talk about building their own cryptocurrency, we see them fighting with each other,” he said. “One of them recently encrypted a hospital filled with cerebral palsy patients, and we see how they are trying to kick this person out for breaking their code.”
The identity of the leaker is not clear, though Holden suggested a Ukrainian cybersecurity researcher was behind the revelations.
If the revelations lead to the end of Conti's domination of the ransomware market, there are still many others standing by to fill that space.
LockBit, a cybercriminal gang that also traffics in ransomware-as-a-service to hackers, released a statement over the weekend, listing some of the many nationalities it counts in its community.
“For us, it is just business, and we are all apolitical,” the group said. “We are only interested in money for our harmless and useful work. We will never, under any circumstances, take part in cyber-attacks on critical infrastructures of any country in the world or engage in any international conflicts.”